Explain Different Types of Hash Functions
Suppose the hash table has 100 memory. For example-if the record.
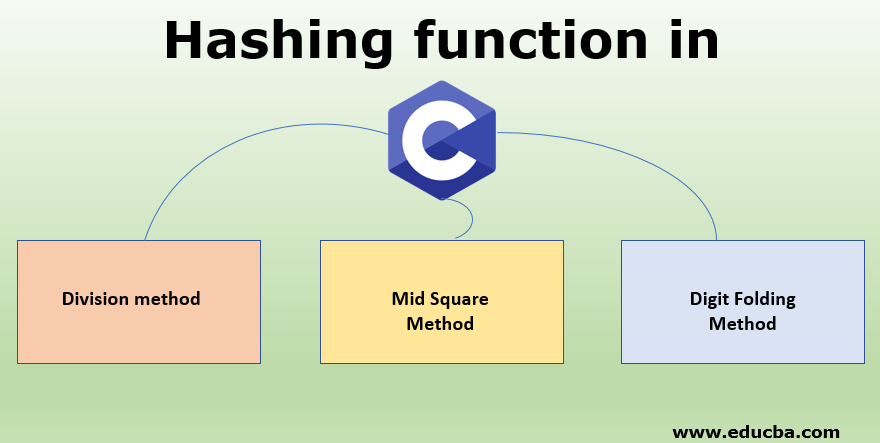
Hashing Function In C Types Of Collision Resolution Techniques
This method is quite good for any value of M.

. MD5 - An MD5 hash function encodes a string of information and encodes it into a 128-bit fingerprint. 32 or 64 bits shiftadd or multadd or shiftaddxor or multxor PJW hash Elf Hash. 32 64 or 128 bits productrotation Fast-Hash.
MD5 was most popular and widely used hash function for quite some years. The load factor of a hash table is the ratio of the number of keys in the table to. A function which for a given data outputs a value mapped to a fixed range.
FirstHashkey i secondHashkey sizeOfTable. A hash function is any function that can be used to map data of arbitrary size to fixed-size values. Here are some of the most commonly used.
Although the Message-Digest algorithm 5 MD5 hashing algorithm was once one of the most popular hashing algorithms available the Secure Hash Algorithm SHA-2 and SHA-3 family of hashing algorithms is now considered the most secure because MD5 generates many. Here keys like MH are given to hash function to generate array integers. A hash function is a mapping function which maps all the set of search keys to the address where actual records are placed.
A hash function algorithm is designed to be a one-way function infeasible to invert. This happened to MD5 for example a widely known hash function designed to be a cryptographic hash function which is now so easy to reverse that we could only use for verifying. The associated hash function must change as the table grows.
The second hash function comes into use when the first function causes a collision. Just like our above example the associative array uses a hash function too. Use of a hash function to index a hash table is called hashing or scatter storage addressing.
For a hash function to be collision-free no two strings can map to the same output hash. The RIPEMD is an. Popular Hash Functions Message Digest MD.
This method divides x by M and then uses the. 32 64 bits xorshift operations SpookyHash 32 64 or 128 bits see Jenkins hash function. It has three different variants SHA-0 SHA-1 and SHA-2.
H K h k x k Here Example. Once a hash value has been generated it must be impossibleto convert it back into the original data. Choose a constant A such that 0 A 1.
Where i is the offset value. This offset value keeps incremented until it finds an empty slot. Weve designed this article to help explain what hashing is.
The MD family comprises of. Hashing is the process of generating a value from a text or a list of numbers using a mathematical function known as a hash functionThere are many hash functions that use numeric numeric or alphanumeric keys. Other than these hash functions mentioned above the user can use any type of hash logic that.
Secure Hash Function SHA. What are the properties of hash functions. The values are usually used to index a fixed-size table called a hash table.
That is the hash function is. If it takes. Different hash functions are given below.
This method leads to poor performance since consecutive keys map to consecutive hash values in the hash table. Associative Array Hash functions. Each of these classes of hash function may contain several different algorithms.
Hash Functions and listtypes of Hash functions. Family of SHA comprise of four SHA algorithms. Hash functions are the building blocks for modern cryptography.
Secure Hashing Algorithm SHA-2 and SHA-3 RACE Integrity Primitives Evaluation Message Digest RIPEMD Message Digest Algorithm 5 MD5 BLAKE2. Some of the major types of hash functions are. Mid square method In this method firstly key is squared and then mid part of the result is taken as the index.
This method has following steps. 32 64 128 or 256 bits. Linear Probing Linear probing is a fixed interval between probes.
Division method In this the hash function is dependent upon the remainder of a division. 32 or 64 bits addshiftxor MurmurHash. However in recent years several hashing algorithms have been compromised.
A hash function is a cryptographic algorithm which is used to transform large random size data to small fixed size data. In this method for creating hash functions we map a key into one of the slots of table by taking the remainder of key divided by table_size. The values returned by a hash function are called hash values hash codes digests or simply hashes.
Hashing is simply the practice of using an algorithm to map data of any length to a fixed-length output. A data structure where the data is stored based upon its hashed key which is obtained using a hashing function. There are many different types of hash algorithms such as RipeMD Tiger xxhash and more but the most common type of hashing used for file integrity checks are MD5 SHA-2 and CRC32.
It provides an offset index to store the value. Since it requires only a single division operation hashing by division is quite fast. But the index number of an array is generated by keys.
Its useful in a number of ways and plays a role in several different types of encryption. Among these three SHA-0 and SHA-1 has been deprecated due to vulnerabilities issues. SHA-0 SHA-1 SHA-2 and SHA-3.
32 or 64 bits XORaddition Bernsteins hash djb2. It is the most simple method of hashing an integer x. In dynamic hashing a hash table can grow to handle more items.
The following are some of the Hash Functions. MD5 is often used as a checksum to verify data integrity. Lets see how this below key-value pair gets stored in the hash table.
In this method the next available data block is used to enter the new record instead of overwriting on the older record. The data output of the hash algorithm is called hash value or digest. H key key mod table_size ie.
Mid Square Hash Function. SHA Secure Hash Algorithm designed by the NSA National Security Agency was used for the digital signature algorithm that consists of 160 bits length. Programmers use different types of hash algorithms depending on the level of security that they desire.
There are several different classes of hash functions. In static hashing the hash function maps search-key values to a fixed set of locations. Other than these depending upon the computational logic the hash function is used to create the resultant hash values there are also different types of hash functions.
The formula for the double hashing technique is as follows.
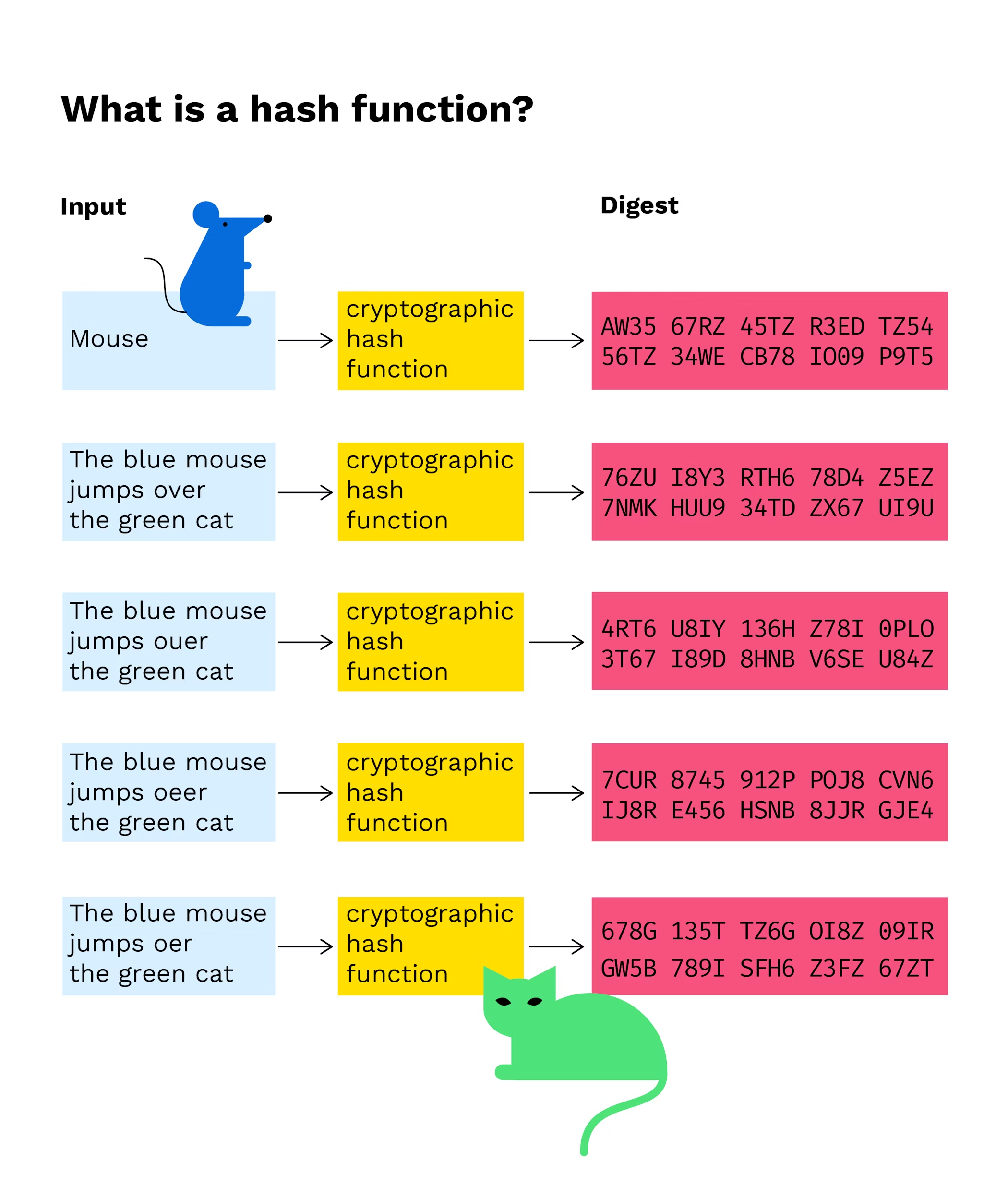
What Is A Hash Function In A Blockchain Transaction Bitpanda Academy
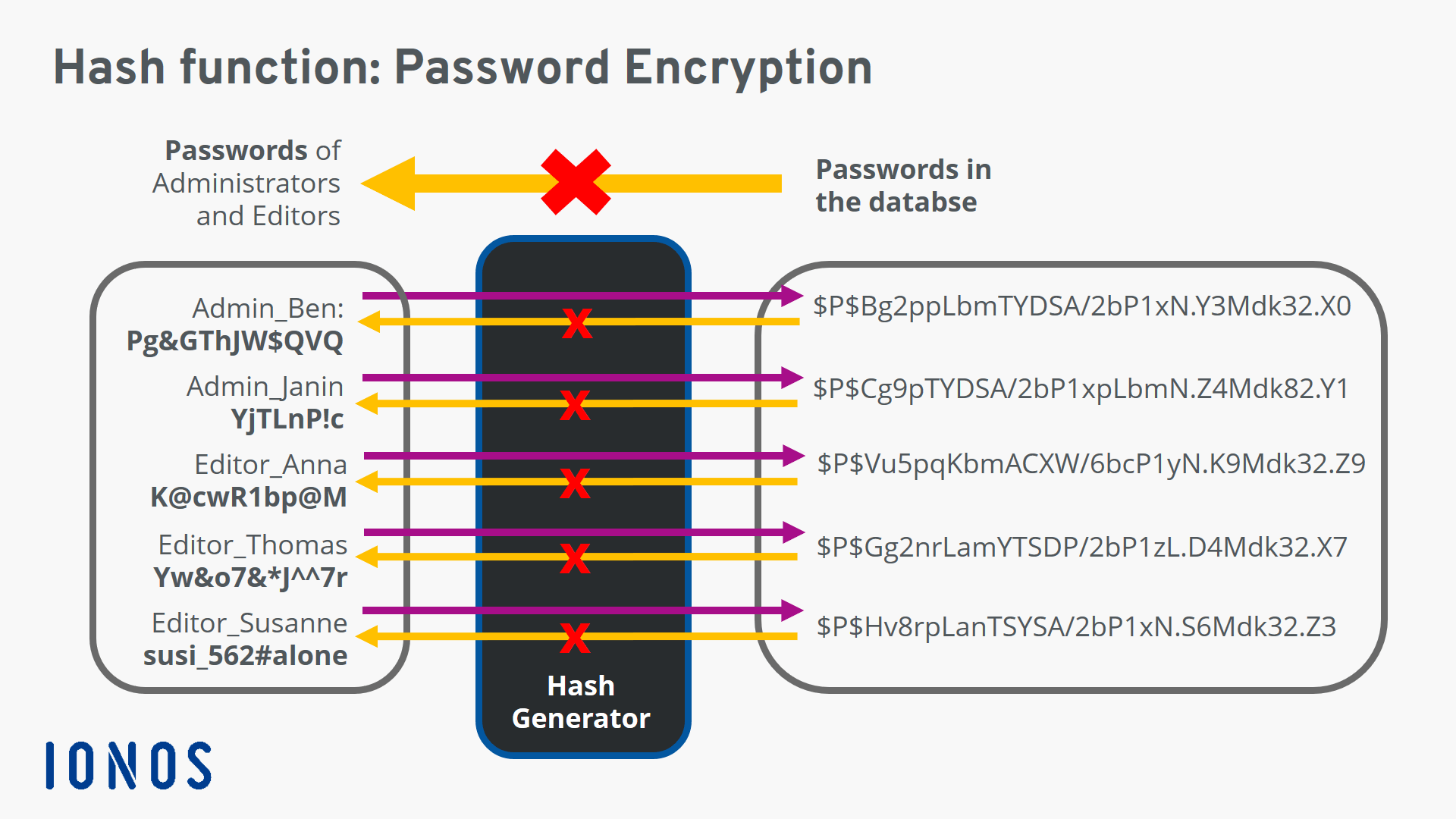

Comments
Post a Comment